In the past we used access cards for identity authentication, but in today's mobile world, applications that embed identity information into a variety of portable devices have been successfully implemented. Virtual credential card technology has revolutionized the industry. Identity authentication is no longer limited to the use of traditional access cards, but extends to many different forms, allowing us to take advantage of mobile devices such as smartphones, USB dongle, memory sticks, microprocessor-based The SmartMX card opens, stores and securely conducts other transactions.
This article refers to the address: http://
HID Global is currently working with handset manufacturers and Near Field Communications (NFC) semiconductor suppliers to embed a new generation of access control technology directly into mobile phones, using virtual credentials to open the door. Not long ago, HID Global announced that it has partnered with BlackBerry maker Research in Motion to configure iCLASS® virtual credentials and mobile security identity technology in NFC-enabled BlackBerry® smartphones. The new technology allows users to exchange information with a new generation of iCLASS SE® readers for identity authentication. In addition, a smart phone with a virtual credential card can be used not only as a key to open the door, but also for mobile payment and other applications.
Arizona State University has implemented the pilot project to use mobile access control technology for the first time in NFC-enabled mobile phones. In August 2011, HID Global deployed iCLASS SE card readers at several dormitory doors of the university, and installed Sargent Profile series electromechanical door locks provided by ASSA ABLOY and supporting HID technology on selected dormitory rooms. . Students and employees participating in the trial entered the dorm using a smartphone embedded with the HID iCLASS® SE virtual credential.

The mobile phone with built-in NFC technology allows the mobile phone and the door lock to exchange access control data. Participants can simply open the door lock by aligning the phone with the card reader in front of the door, using the same method as the previous iCLASS access card. The technology also supports air configuration and digital key management, simplifying the management of access control systems.
Break through the traditional smart card mode <br> <br> as technology advances, access cards can be more complex applications. Just like today's 13.56 MHz contactless smart card, not only can the cardholder be bound, but also the dual authentication with the card reader to ensure security. In addition, the secure storage capabilities of contactless smart cards enable a wide range of applications, such as biometrics, small electronic payments, and secure PC desktop logins. Until now, we still need such cards to identify the access control system rules stored between the card reader and the central controller for secure identification to determine whether to open the door.
As we enter a new era of increased mobility, more advanced applications, and increasing security threats, the industry is moving toward a new generation of portable authentication access control architectures. A new generation of access control technologies such as iCLASS SE enable credential cards to be securely embedded in fixed and mobile devices and security settings that not only improve security, but also enable access control technology to be applied to virtual credential cards.
The first step in supporting portable authentication is to establish a reliable identity authentication framework that verifies all end devices in the network (such as credential cards, printers, card readers, and NFC-enabled phones) so that data between end devices can Secure transmission. HID Global's Trusted Identity Platform (TIP) is one of the frameworks that support secure data transfer. TIP builds a scalable framework and delivery infrastructure that delivers three key capabilities: a secure, secure channel between hardware and software; optimal key management and security setup processes; and seamless integration with IT infrastructure.
A trusted framework must have a secure, open, and independent Secure Identity Object (SIO) data structure on the side of the certificate card; and a corresponding SIO decoder on the side of the reader. SIO is a standards-based, device-independent data object that can be stored on any number of authentication devices. The SIO and SIO decoders perform similar functions to traditional cards and card readers, except that the data structures used are safer and more flexible.
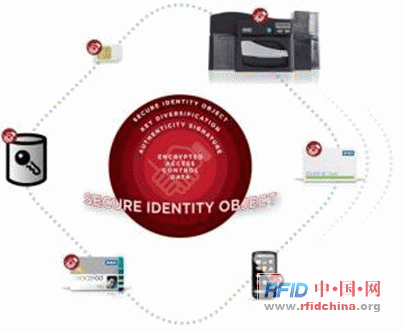
SIO has three advantages: portability, security, and scalability. First, because SIO is portable, it can be placed on traditional contactless credential cards, memory cards with other card technologies, microprocessor-based cards such as SmartMX, and NFC-enabled smartphones. , USB dongle, computer hard drive and many other forms of interface. This enables data objects stored in one device to be easily and unimpededly ported to another device, thereby achieving interoperability.
Secondly, the device-independent SIO adds a layer of security to the security of the device, adding a layer of protection to the data. This layer of protection provides additional diversification keys, authentication and encryption to prevent Security has been compromised. In addition, by using the unique features of the device, the data object is bound to a specific device to prevent the card from being copied.
Third, SIO is defined by open standards, including the ASN.1 standard, which is jointly developed by ISO/IEC and ITU-T and is a data definition that allows the definition of data objects to be infinitely scalable. This infinitely scalable definition supports any data segment, including data for access control, biometrics, small electronic payments, attendance, and many other applications. Unlike many other fixed field structures used in today's access control cards and reader systems, the field structure used by SIO and related decoders allows for increased security features, while traditional architectures are lagging behind, stagnating, and fixed definitions. limit. In addition, as mentioned earlier, due to this flexible SIO data definition, customers have the flexibility to adopt security measures.
Future applications <br> <br> market more and more high-end smart phones with NFC technology, along with increased use of electronic payments and NFC-enabled mobile phone prices decline, NFC smart phones will be more popular. According to IHS iSuppli market research company, there are about 93 million NFC mobile phones delivered globally in 2011, and will increase to 500 million by 2015, that is, 30% of mobile phones in the world have NFC functions.
NFC smartphones will bring more virtual voucher-based applications in the future. Although today's airlines use convenient QR code technology, travelers have shown interest in using their smartphones as boarding passes. This further confirms that the use of today's mobile phones to complete various transactions is becoming more and more popular.
At present, many Japanese fast food restaurants, subway stations, taxis and vending machines have installed NFC payment systems. College students can not only use the NFC-enabled smartphones to get in and out of the building, but also use them to pay for parking, shopping, boarding a school bus, borrowing library materials, and verifying their identity when taking exams and logging into a computer. In the future, it is also expected to use the NFC smart phone to make electronic payments at electric vehicle charging stations. The driver drives the car to the charging meter, uses the charging service and pays the service fee through the NFC-enabled mobile phone, or allows the medical institution to view the patient health record through the smartphone. When the patient visits the hospital, he or she can present the information to the medical staff by presenting his or her mobile phone without having to fill out the form.
The portable authentication credentials card will make it easy for users to obtain, provide, share and modify personal electronic keys stored in the electronic wallet. With access control information and record keeping and NFC-enabled mobile phones, rather than in the door lock, users are more likely to secure places and items. The system can remotely cancel the virtual credential card stored in the smartphone, re-issue the voucher, and change the person and time that can use the virtual credential. Virtual credential card technology will create a more convenient and secure trading platform for opening, shopping and other transactions.
Cordless Floor Cleaner is a new and smart vacuum mopping cleaner. recharge floor cleaner very small,free,simple use. Latest floor wipe cleaner can vacuum ,mopping,wipe home,hotel,office clean area.recharge mopping cleaner very good design,use simple and freely,
Wireless hand floor cleaner advantage:
Cordless hand floor cleaner with special design and best quality
Vacuum ,mopping function
Fast and silent and smart floor hand cleaner
Cordless floor cleaner facotry in shenzhen,china,welcome to visit facotry,we are 15 years manufacture experience.
Cordless Floor Cleaner
Cordless Floor Cleaner,Robot Vacuum Cleaner,Cordless Hard Floor Cleaner,Cordless Floor Cleaning Machine
Zhengzhou Bangmi Smart Technology Co., Ltd. , https://www.globalcleanrobot.com