Tag: Wireless Data P2P
This article refers to the address: http://
1 Introduction
P2P (Peer to Peer) technology is an application mode that shares resources and services by directly exchanging between systems. In the P2P network structure, each node has the same status, and has dual functions of client and server, and can serve as both a service user and a service provider. P2P is not only a technology, but also an idea that embodies the essence and characteristics of Internet equality, openness, and freedom.
In recent years, P2P applications represented by BT, emule, etc. have developed rapidly. The development of instant messaging, streaming media and Internet IP telephony based on P2P is also very rapid. P2P applications have surpassed Web applications in the fixed Internet, occupying More than 50% of fixed Internet traffic. In the current mobile Internet environment, mobile P2P applications have not been implemented due to network and terminal restrictions. However, with the continuous development and evolution of mobile networks and the increasing processing capabilities of mobile terminals, P2P technologies and services will gradually expand. To the mobile internet. This paper will discuss the application of P2P technology in the mobile Internet environment.
2. Main features of P2P technology
An essential difference between P2P technology and the dominant client/server architecture in the current network is that there is no central node (or central server) in the entire network structure. P2P technology has four main features.
(1) Decentralization. A pure P2P network has no central service nodes. All Peer is both a client and a server. This is one of the most essential features of P2P. In the P2P technology structure, the meaning of the center is greatly weakened or even completely disappeared, and the characteristics of decentralization are more fully reflected, and the flattening of the network structure is further highlighted. Many P2P applications use a hybrid approach due to the complete decentralization that creates implementation and management difficulties.
(2) Scalability. Scalability is considered to be one of the most important features of P2P networks, and P2P networks can theoretically be extended indefinitely. Emule currently has tens of millions of users worldwide, and the number of BT users exceeds that of emule, and it is still growing rapidly.
(3) Robustness. The P2P network architecture is inherently resistant to attack and high fault tolerance. Since the service is distributed among the nodes, the destruction of some nodes or networks has little effect on other parts. Like the failure of the central node in the traditional network structure, the phenomenon of all services is almost impossible.
(4) High cost performance. The P2P architecture can effectively utilize a large number of common nodes scattered in the Internet, distribute computing tasks or storage data to all nodes, and utilize idle computing power or storage space to achieve high-performance computing and mass storage. A large amount of idle resources can provide higher computing and storage capacity at a lower cost.
Based on the above characteristics, typical applications of P2P technology include: file and content sharing, such as Napster, emule, BT, etc.; distributed computing and storage sharing, such as SETI@home, Avaki, Popular Power, etc.; collaborative processing and service sharing platform, For example, JXTA, NET My Service, etc.; communication and collaboration, such as Skype, MSN, OICQ, etc.
3. Implementation of P2P application in mobile environment
3.1 The structure and characteristics of the mobile Internet
The mobile Internet logical structure based on GPRS/EDGE/WCDMA is shown in Figure 1. The packet domain network element mainly has SGSN and GGSN, and the main interfaces include Gn and Gi. The SGSN connects to the wireless subsystem and the core network packet domain, and connects to the GGSN through the Gn interface, and the GGSN connects to the external data network through the Gi interface.
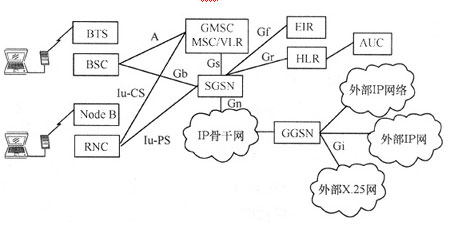
Figure 1 Mobile Internet logical structure
Compared with the fixed Internet, mobile networks have some unique mechanisms and features, which may affect the application and development of P2P technology in the mobile Internet. There are four main aspects.
(1) The wireless data channel of GPRS/EDGE/WCDMA adopts time division multiplexing mode for uplink and downlink symmetric configuration, but due to the characteristics of current mobile internet applications, some mobile terminals adopt asymmetric data transmission mode (2+1 or 4+). 1) The uplink and downlink traffic within the mobile Internet is quite different. Statistics show that the ratio of downlink data traffic to uplink data traffic in GPRS network is about 4.5:1, and the ratio after EDGE is 6.4:1. The relative idleness of the uplink channel is objectively beneficial to P2P applications in file and content sharing. .
(2) The GPRS packet service channel can adopt different coding modes of CS-1 to CS-4, and the maximum transmission rate is 171 kbit/s. EDGE uses 8PSK (8-phase phase shift keying) modulation technology. If 8 time slots are concentrated, the data transmission rate can reach 450 kbit/s. The transmission rate in 3G networks can reach 2 Mbit/s. If HSDPA technology is used, the theoretical downlink rate of 14.4 Mbit/s can be achieved. However, compared with the fixed Internet, the transmission rate of the mobile Internet has a huge gap, and the P2P application in the fixed Internet is difficult to simply transplant into the mobile Internet environment.
(3) In the fixed Internet, both parties that can use the P2P service are in a network connection state, and each has a separate IP address that can be used. In the mobile Internet environment, whether the dynamic or static IP address allocation method is adopted, the IP address of the mobile terminal can be effective only when the PDP (Packet Data Protocol) context activation is completed, that is, both parties using the P2P application must complete the PDP activation. If the service provider is not in the PDP context activation state, the network side initiates the PDP context activation function, and the PDP context activation process is initiated from the network side device.
(4) The mobility of the terminal is a significant feature of the mobile Internet. When the mobile terminal switches from one GGSN to another GGSN, the IP address of the terminal will be redistributed, which will impose certain restrictions on the application of P2P technology. At the same time, it affects the structure of the P2P network to a certain extent, and thus it will have certain influence on the query and routing mechanism in the P2P network. In addition, the processing power, storage space and other restrictions of the mobile terminal CPU are not suitable for many successful P2P applications (such as transmission and sharing of large files), so in the mobile Internet, some optimized ones should be developed according to the characteristics of the mobile terminal. P2P business.
3.2 Solutions for deploying P2P applications in a mobile environment
With the continuous improvement of the performance of mobile terminals, it is undoubtedly very attractive to directly apply P2P services on mobile terminals. There are two difficulties in deploying P2P applications on mobile terminals. One is the problem of P2P client software on the mobile terminal, and the other is the problem of deploying P2P applications in the mobile network.
At present, there are many operating systems for mobile terminals. The mainstream operating systems include Symbian, Linux, Windows Mobile, etc. If you want to use P2P applications on mobile terminals, you must develop different versions of applications or client software based on the general protocol. This requires not only a unified mobile P2P protocol standard, but also the opening of each mobile phone terminal manufacturer for their respective platforms.
Due to the processing power and memory limitations of the mobile terminal, the P2P request cannot be sent in the infinite flooding mode in the mobile network, and the hybrid mode architecture is more suitable for the mobile Internet. In addition, the application range of the P2P is preferably also limited according to the service situation. For example, the P2P service can be applied within the range of the mobile terminal's address book. At this time, a problem arises. The friends in the address book are identified by the mobile phone number instead of the IP address. In the mobile Internet environment, in most cases, the IP addresses obtained by the mobile terminal are dynamically allocated. Since the mobility of the terminal may cause the IP address to change, a dedicated node is required in the network to query, record, and track the correspondence between the mobile phone number and the IP address.
The P2P proxy server is implemented in the mobile Internet to implement the P2P proxy server. The main functions of the P2P proxy server include: registration management of the P2P service, initiation of the PDP context activation on the network side, and maintenance of the correspondence between the mobile phone number and the IP address. In order to realize the integration of mobile terminal and fixed Internet P2P service, P2P proxy server can also act as a proxy for mobile P2P applications and fixed-line P2P applications, and implement protocol conversion and other functions, so that P2P services can be seamlessly integrated in fixed Internet and mobile Internet. The mobile P2P server can be implemented on the existing GGSN only from the perspective of function implementation.
Due to the characteristics of the mobile Internet, the P2P service should be independent of the evolution of the access network. Whether the user accesses through the 2.5G GPRS network or through the 3G WCDMA network, the mobile terminal can use the mobile P2P service normally.
3.3 Mobile P2P Service Implementation Process
Assume that the operator opens a "mobile podcast" service, and the user uses the mobile terminal to take some interesting videos and save them in their mobile phones for sharing with friends in their own communication records. The following is a specific service implementation process to illustrate how to implement a mobile P2P application by introducing a P2P proxy server in the mobile Internet.
Assume that User A has opened the "Mobile Podcast" service and shared some of the video clips he has taken. User A now hopes that his friend B in his mobile phone directory can enjoy his masterpiece. Then, the user A sends the request through the P2P software in the mobile phone. After receiving the request of the user A, the P2P proxy server goes to the network to query the status of the user B. If the user B has not performed the PDP activation, the PDP activation of the network side can be initiated, and then The IP address obtained by the user B is sent to the user A, and the request of the user A is sent to the user B. After receiving the notification that the user A requests to enjoy the personal podcast, the user B can see the video captured by A through the mobile terminal.
Suppose that there are multiple users to appreciate the content in User A's "Mobile Podcast", and User A's terminal cannot meet the needs of all users due to processing capacity limitations. According to the P2P network management and scheduling mechanism, the mobile P2P proxy server will These users' requests are sent to users who have already visited the "Mobile Podcast" service (such as User B), who serve as a service provider to satisfy some of the business requests.
At the same time, the user C of the fixed Internet can also use the client software of the PC to use the protocol conversion and proxy function of the mobile P2P proxy server after entering the mobile phone number of the A, in the same way to enjoy the "mobile podcast" of A. Content, the integration of fixed Internet and mobile Internet P2P services.
4. Challenges and countermeasures
Due to the inherent characteristics of P2P technology, P2P services have encountered some obstacles and challenges in the rapid development of fixed Internet, such as intellectual property protection, network security, unified standards, traffic and billing. Therefore, while deploying P2P applications on a large scale in the mobile Internet, in order to ensure and promote the healthy development of the business, we must face these obstacles and challenges and explore solutions in a targeted manner.
(1) Intellectual property protection
P2P services will inevitably conflict with intellectual property rights. Every P2P application that provides shared services needs to carefully examine the copyright issues faced by P2P networks. In terms of copyright protection, DRM (Digital Rights Management) is a viable method. It can control the distribution, transmission and use of digital products, so that digital products can only be used by authorized persons within the authorized use period. In addition, the real-name system for mobile phones that is currently being implemented will also help resolve copyright issues.
(2) Network security issues
The network security problem is not caused by the introduction of P2P technology, but the equal sharing of P2P technology will make this problem even worse. At present, viruses, spam and hacker attacks against mobile terminals continue to emerge, posing serious challenges to the network security of mobile Internet.
There are two ways to solve this problem: on the one hand, mobile network operators deploy network security devices centrally within the core network to filter and intercept viruses and spam; on the other hand, they provide mobile terminals with similar use in current PCs. Firewall and anti-virus software. However, these two methods have certain limitations. The ideal method is to use the current enterprise-level virus-killing software. Mobile network operators deploy security and anti-virus servers in a centralized manner, and are responsible for timely updates. Mobile terminals download and install customers. And use the mobile Internet to update. Of course, the above process can also be implemented by means of P2P.
(3) Lack of uniform standards
At present, a bottleneck in the development of P2P technology is the lack of unified standards. The divergence of interests makes it difficult to form a unified standard, which creates artificial obstacles for the promotion of P2P, which is contrary to the original intention of P2P's freedom and equality.
Since the current mobile P2P is still in its infancy, the standard unification problem is relatively easy to solve. Mobile operators can refer to the development model of Monternet, dominate the upstream and downstream of the value chain, and develop a unified mobile P2P technology standard, paving the way for the application of P2P technology in the mobile Internet.
(4) Traffic and billing issues
For mobile operators, wireless resources are very valuable. How to balance P2P services and wireless resource consumption is a key issue. The specific approach is to select P2P services with small service traffic between nodes, and restrict the information traffic between these nodes through certain methods. For example, for P2P-based file sharing systems, P2P services based on flooding method are not used. To avoid the size of the P2P network is too large, while strictly limiting the size of shared files.
The fixed-net billing method using the monthly subscription has greatly promoted the development of P2P services. However, the mobile Internet is currently charged according to the uplink and downlink traffic. This charging mode is almost fatal for P2P services. No one is there. Willing to pay for upstream traffic generated by others. Therefore, on the basis of content charging, the monthly subscription of services with certain basic traffic is very necessary for the development of mobile P2P services.
5, the conclusion
P2P technology and applications have achieved great success in fixed Internet, but the application in mobile Internet has not yet begun. Due to the inherent structure and characteristics of mobile Internet, P2P technology is difficult to simply transplant from fixed Internet to mobile network. With the continuous evolution of mobile networks and the continuous improvement of the performance of mobile terminals, the demand for implementing P2P applications in the mobile Internet environment has also become increasingly prominent. Based on the characteristics of P2P technology and mobile Internet, this paper makes a preliminary analysis of the application of P2P technology in mobile internet, discusses the implementation of P2P application by deploying P2P proxy server in mobile network, and discusses it from the perspective of technology and business. The challenges and solutions brought by the introduction of P2P technology in the mobile Internet.
APM Variable Power Supply inherits the functional design and maintains the high power density characteristic.Standard communication interface includes RS232/RS485/USB/LAN,GPIB is optional.Users can choose the Switch Mode Power Supply that fits their testing requirements perfectly.
Some features as below:
- With accurate voltage and current measurement capability.
- Coded Knob, multifunctional keyboard.
- Standard RS232/RS485/USB/LAN communication interfaces, GPIB is optional.
- Remote sensing line voltage drop compensation.
- Equips with LIST waveform editing function.
- Use the Standard Commands for Programmable Instrumentation(SCPI) communication protocol.
- Have obtained CE certification.
150V Dc Source System,High Current Power Supply,Apm Tech Power Supply,150V Dc Power Source
APM Technologies (Dongguan) Co., Ltd , https://www.apmpowersupply.com