Industrial control systems have a wide range of applications in process production, power facilities, hydropower, and transportation. The security of traditional control systems relies heavily on the privacy of their technology, with almost no security measures taken. With the increasing attention of corporate management to production process data, industrial control systems are increasingly using open lnternet technology to interconnect with enterprise networks. Currently, most industrial communication systems develop protocols based on commercial operating systems, and there are many vulnerabilities in communication applications. These vulnerabilities will be exposed to potential attackers when industrial control systems are interconnected with the Internet or other public networks. In addition, industrial control systems are often used to control critical infrastructure measures, and attackers will actively attack them for political or economic purposes with a view to causing serious consequences. For example, in 2010, the "Shenzhen" virus swept the world, and the Iranian Bushehr nuclear power plant was postponed due to this attack. Therefore, in recent years, the information security problem of industrial control systems has become a hot issue of widespread concern.
This paper firstly combines the characteristics of industrial control systems, analyzes the requirements of control systems and the threats and attacks they face, and then introduces the current information security solutions from the perspective of network protection, and introduces relevant research trends, including the relevant standards. Secure communication protocol and security controller.
1. Information security analysis of industrial control systems
1.1 Overview of Industrial Control Systems
Industrial control systems are systems that use computers as a basic component to monitor and control physical processes. This type of system contains a networked system in which most network systems are connected to physical systems. Depending on the scope of application, the control system can be further divided into Process Control System (PCS), Monitoring and Data Acquisition System (SCADA), or Network-Physical System (CPS).

A control system typically consists of a series of network devices, including: sensors, actuators, process control units, and communication devices. The control system usually adopts a layered structure. The typical control system network structure is shown in Figure 1. The first layer is the physical facility where field devices such as sensors and actuators are installed. The field devices are connected to the programmable logic controller through the fieldbus network ( PLC) or remote terminal equipment (RTU) connection, PLC or RTU equipment is responsible for implementing local control functions. The second layer is the control network and is responsible for real-time data transmission between the process controller and the operator station. The operator station is used for area monitoring and setting of physical facility settings. The third layer is the enterprise network, and the enterprise workstation is responsible for production control, process optimization and process log recording.
According to the application characteristics of the control system, it can be divided into safety-related applications and non-safety-related applications. Once a safety-related application fails, it can cause irreversible damage to the controlled physical system. If such control systems are damaged, they will have a major impact on public health and safety and lead to economic losses.
1.2 Safety requirements for industrial control systems
The traditional IT information security technology is relatively mature, but because of its many differences between the application scenarios and the control system, it cannot be directly applied to the information security protection of the control system. This section focuses on the difference between control systems and traditional IT information security, analyzes the unique attributes of control system information security, and proposes new challenges for control systems.
One of the characteristics of the control system is the requirement for usability. Therefore, the software patching method and system update frequency of traditional information security are no longer applicable to the control system. For example, a system upgrade of a control system needs to be scheduled a few months in advance, and the system needs to be taken offline when updating. Moreover, in industrial applications, the economic cost of a shutdown update system is high. In addition, some system patches may also violate the rules of the control system. For example, on March 7, 2008, a nuclear power plant suddenly stopped because a computer in the system that monitors factory data was restarted after a software update. After the computer restarts, the data in the control system is reset to the default value, causing the safety system to think that the temperature of the water used to cool the nuclear fuel rod drops.
Another feature of the control system is the requirement for real-time performance. The main task of the control system is to automatically make real-time judgments and decisions on the production process. While traditional information security has a lot of research on usability, real-time availability requires a more rigorous operating environment. For example, traditional IT systems often use measures such as handshake protocol and encryption to enhance security. In the control system, adding security measures may seriously affect the responsiveness of the system, so traditional information security technologies cannot be directly applied to the control system. In order to ensure the security of the control system, the control network needs to implement relevant security mechanisms and standards, which requires the network to meet certain performance requirements.
In addition to the above two characteristics, the biggest difference between the control system and the traditional IT information system is that the control system has an interactive relationship with the physical world. In general, many technical measures and design guidelines in information security are relatively mature, such as authentication, access control, message integrity, and minimum permissions. Using these proven technologies can help us defend against attacks against control systems. However, computer security mainly considers the protection of information, and there is no research on how attacks affect the physical world. Moreover, industrial control systems have limited resources and long life cycles, and cannot directly transplant traditional IT information security technologies. Therefore, although current information security tools can provide the necessary defense mechanisms for control systems, relying solely on these mechanisms does not provide sufficient depth protection for the control system.
Of course, compared with traditional IT systems, the control system also has more easy-to-operate features, which facilitates the design of system security mechanisms. The network dynamic characteristics of the control system are simpler, with fewer server changes, fixed network topology, fixed user population, fixed communication type, and fewer communication protocols.
1.3 The threat of industrial control systems
The threats to industrial control systems can be divided into two types: system-related threats and process-related threats. Typical system-related threats and process-related threats are shown in Table 1.
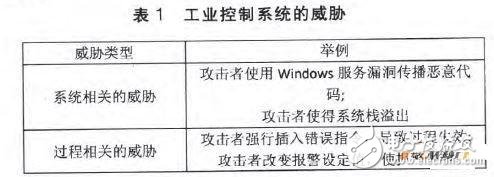
System-related threats are threats caused by software vulnerabilities. The control system is broadly an information system that is subject to system-related threats such as protocol implementation vulnerabilities and operating system vulnerabilities. In the CCSP2009 report of the Control System Security Project, the system-related threats of the general control system are classified into nine types through the CSSP security assessment. Table 2 lists these nine security issues.

Process-related threats are attacks that industrial control systems experience during production. This type of attack exploits the characteristics of process control. After an attacker illegally obtains user access rights, it issues legal industrial control system commands, causing industrial process failures. Based on the interaction point between industrial control system users and industrial processes, process-related threats can be divided into two categories: 1 threats affecting access control of field devices; 2 threats affecting the central console. The former usually sends incorrect field data to the control system status monitoring center, which causes an error in the system status analysis. The latter usually enforces legitimate commands at the central console, but the order is unreasonable for the production process and will have a negative impact on production or equipment.
Once the vulnerability of the control system is exploited by an attacker, it will be subject to different types of attacks. The specific attack forms can be divided into:
1) Spoofing attack: Disguised as a legitimate device during communication. For example, use a fake network source address.
2) Rejected service attack: Any resource in the system is unavailable. For example, a device is too busy to respond to a large amount of malicious traffic and cannot respond to other messages.
3) Man-in-the-middle attack: The attacker intercepts all messages from one end of the communication, and then modifies the message and then forwards it to the terminal receiving device.
4) Replay attack: repeatedly send an outdated message, such as user authentication or command.
2. Information security solution for industrial control systems
In order to prevent industrial control systems from being subjected to the above various threats and attacks during communication, multiple layers of security measures are required to complete the protection of the system. Based on the existing research results, this paper introduces the information security solution of control system from the aspects of network boundary protection, security protocols and security controllers.
2.1 Network boundary protection
The system threat of the industrial control system mentioned above is caused by the traditional IT technology, such as operating system, Web server, and mailbox vulnerability. On the other hand, the control system is interconnected with the enterprise network and exposed to the public network. Among them, there are more attacks. Therefore, in order to ensure the security of industrial control systems, it is first necessary to enhance the protection of network boundaries to reduce the risk of threats introduced by enterprise networks. The standard SP800-82 "Industrial Control System (ICS) Safety Guide" states that when dealing with the connection problem between the industrial control system network and other application networks, it needs to be designed according to the principle of minimum access. It is divided into two suggestions:
1) When the industrial control system deploys the network, it is recommended to isolate the industrial control system from other enterprise networks. Usually, the traffic of these two types of networks is different, and the enterprise network does not specify strict control procedures for network equipment changes; if the industrial control system network traffic exists on the enterprise network, it may suffer a denial of service attack. Network isolation can be achieved by using technologies such as firewalls.
2) If a connection must be established between the industrial control system network and the enterprise network, only one connection is allowed to be established as much as possible, and the connection is implemented through a firewall or a demilitarized zone. In terms of specific technical measures, SP800-82 details the available technical measures from the aspects of identity authentication, access control, auditing and verification, system and communication protection.
(1) Identity authentication
Verify the device or person you are requesting access by PIN or password. The password needs to be encrypted when transmitting the password on the network, and the replay attack can be blocked by selecting an appropriate cryptographic hash function. Password authentication can also be supplemented by other authentication measures such as asking/responding or using biometric tokens or physical tokens. In an emergency, there are certain risks associated with the use of passwords and biometrics in industrial control systems. Therefore, in the case where the password is not suitable, strict physical security control can be used instead.
(2) Access control
Role-based access control (RBAC) can be used to restrict a user's permissions so that they can complete tasks with minimal privileges. System administrator communications need to be authenticated and protected for confidentiality and integrity, such as using SSHv2 and HTTPS protocols. Both protocols use a public/private key pair for user authentication. Both parties to the communication generate and use a symmetric key to encrypt the data interaction process.
The RADJUS remote authentication dial-up user service is currently the most used authentication and authorization service. It uses IEEE802.1 & TImes; and EAP protocol to implement user authentication at all layers of the network. For example, firewalls and access routes can act as authentication agents.
When the wireless device or the interrupted user device needs to be connected to it, the authentication agent issues an inquiry to the device, and the device returns the authentication information through the authentication server, thereby obtaining the authorization and access permission.
Modems are often used to provide backup connections. The callback system confirms whether the dialer is a legitimate user through the callback number stored in the database. The remote control software requires a unique username and password, encryption and audit logs. Neighbor authentication at the link layer needs to be implemented using the CHAP protocol.
The link between wireless user access and network devices can be implemented in a variety of ways, such as the IEEE 802.11b/g network access point approach. All wireless communications require strong encryption, such as AEP encryption in IEEE 802.11i. Wireless access requires the use of IEEE 802.1x certified customers.
(3) Audit and verification
The industrial control system needs to be periodically audited. The verification includes: the safety control measures in the test phase are still installed and used in the production system; the production system is not damaged by security, and if it is damaged by security, the information of the attack is provided; Changes to establish records of review and approval.
Periodic audit results are expressed in terms of metrics used to show security performance and security trends. Auditing requires the use of specific tools for record maintenance and requires component support in industrial control systems. Auditing helps maintain the integrity of the industrial control system over the life of the system. Industrial control systems need to provide reliable synchronization timestamps for audit tools. Logs maintained in industrial control system applications can be stored in multiple locations, with or without encryption.
(4) System and communication protection
System and communication protection can be achieved through network protection measures such as firewalls and intrusion detection systems, as well as data encryption such as VPN. The network firewall controls data traffic between network areas of different security levels. NIST SP 800-41 provides guidance on firewall selection and firewall policies. In an industrial control system environment, a firewall needs to be deployed between the control network and the enterprise network. The features included in the firewall include: event logging, intrusion detection systems, demilitarized zone based routing, access lists, and more.
The intrusion detection system issues an alert when the system is sniffed or attacked. Intrusion detection systems detect malicious traffic by analyzing information at various key points in the network, alerting, discarding invalid data, logging events and activities, and triggering other security responses. For attacks on application protocols in a variety of industrial control systems, such as DNP and lCCP, intrusion detection systems also add corresponding attack signatures.
An IPSec-based VPN can provide a secure tunnel for communication at the network boundary, usually on a corresponding firewall. IPsec guarantees integrity, authentication and data confidentiality. At the tunnel entrance, an extra packet header is added outside the IP packet. The router forwards the data using the new header information. When the tunnel exit is reached, the original IP packet is extracted. In the user authentication process, IPSec usually uses a private key and RSA signature. Use MD5 or SHA hash functions for message authentication and integrity protection. In data encryption, AES or 3DES.IPSec is also used as a symmetric key derivation using Diffie-Hellman. IPSec devices use the IKE protocol to authenticate other devices, negotiate and assign symmetric encryption keys, and establish IPSec secure connections.
Security management of the control system includes detection, analysis, provision of security and incident response. Specific content includes dynamic adjustment of security requirements, prioritization of security vulnerabilities, and mapping of security requirements to security management: authentication and authorization servers, security keys, traffic filtering, IDS, login, etc. SNMP is used to manage IP network resources such as routing, firewalls, and servers. SNMP can also be used to provide centralized management of the control system network. The security features included in SNMPv3 are message integrity, authentication, and encryption. SNMPv3 uses MD5 and SHA hash algorithms and DES and AES encryption algorithms.
(5) Other measures
In order to ensure the reliability of network operation, industrial control systems need to set redundant topology and functions. Ethernet and IP networks are mostly used as communication protocols in industrial control systems. Redundancy of the Ethernet layer can be achieved by using the mesh topology in the RSTP protocol within the local area network. The redundancy of the IP layer is through backup links between routes, such as OSPF dynamic routing protocol, and IP network redundancy, such as VRRP. MPLS provides reliable data transmission for virtual arbitrary protocol data in IP networks. Tunnels such as the L2TP protocol can also provide reliable transmission of data in an IP network.
The clocks and network devices in the control system need to be accurately synchronized, and the event log records also need to record the exact time. The NTP protocol and the IEEE l588 protocol can be used for time synchronization. The NTP protocol is widely used in the Internet, and the IEEEl588 protocol mainly satisfies the requirements of the control system for clock synchronization. Both of these protocols can be serviced by standalone devices or by components of other network devices.
2.2 Protocol Security
Industrial communication protocols, such as the MODBUS protocol, did not take security measures when designing the protocol. However, as the connection between the control system and the external network increases, it is necessary to increase the authentication process of both parties. The security of the protocol can be improved in two ways. One is to directly modify the protocol and increase the authentication function. The other is to increase the information security layer without modifying the existing protocol.
The document designed an authentication-type Modbus protocol, which enhances the authentication function of the Modbus protocol by using an encryption function and a hash chain for messages, so that an attacker cannot masquerade as a host. At the same time, a compression function is used to reduce the data storage size. This method can increase the authentication process of the protocol for both parties, but at the same time increase the communication burden. That is, the message transmitted by each call needs to be encrypted and authenticated, which may not meet the real-time requirements of the control system. Therefore, it is necessary to consider both computational efficiency and computational cost in design.
The literature draws on the concept of functional safety and proposes a method to add an information security module on top of the communication system. Functional safety of the control system The functional safety layer is added on the basis of the transmission system, and the system fail-safe can be realized without changing the underlying transmission system. Similarly, the document designs an information security module to protect the authentication, integrity, and confidentiality of end-to-end communications. The so-called security module does not refer to a simple physical module, but corresponds to the device model in PROFINET IO and is a software implementation. As shown in FIG. 2, the security module obtains process data from the application layer, encrypts the process data through an encryption algorithm, and uses the MD5 algorithm to calculate message integrity coding. The status byte is used to indicate message integrity and timeout. The security module can be adapted to different security requirements and different computing capabilities through parameterization. Message integrity coding can prevent man-in-the-middle attacks. For example, an attacker intercepts a sent message and tampers with the process data. Since there is no key, an accurate message integrity code cannot be calculated, and the recipient verifies the MAC after receiving the message. Failure to verify its correctness will modify the status byte to report the attack status.
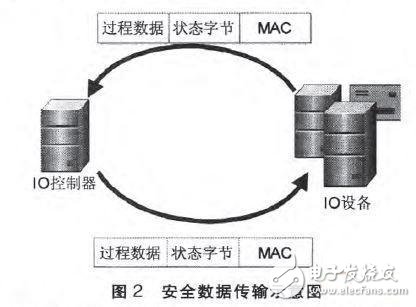
The security module is a software layer placed on top of PROFINET IO and can only be used to defend against network-based attacks, but not for device security. If the attacker gains control of the device, the data is manipulated and the security module will not work. Therefore, the security module can be combined with device security measures to address device and network security.
The security of the protocol is mainly embodied in the encryption processing of the transmitted data, ensuring the integrity and confidentiality of the message, and realizing the secure authentication of the device. In practical applications, two influencing factors need to be considered. On the one hand, due to the large amount of computation of encryption measures, the real-time communication and the available resources of the system will be affected. Second, it is necessary to design a reasonable and effective key management method.
3. Controller design
The above describes two security problem solving ideas from the perspective of network protection and communication protocols, but it is essentially the protection of information. Regardless of the type of attack, the ultimate goal is to achieve damage to the physical facilities. Therefore, it is necessary to study the impact of the attack on the state prediction and control algorithms of the system, and design defense measures from the perspective of the physical system.
In order to understand the interaction process between the control system and the physical world, it is first necessary to analyze the impact of the attack on the physical system. Secondly, based on the control commands and the measured values ​​of the sensors, predict the phenomenon that the physical system should have, so as to judge whether it is affected by the attacker; The controller algorithm is designed with the attack factor in mind, and a control algorithm that can resist the attack is designed.
The literature analyzes replay attacks and integrity attacks, and uses Kalman filtering and x2 fault detection to detect whether the system is attacked. This detection method is based on a physical model and can be used as a complement to intrusion detection based on network and computer system models. When designing detection algorithms, you need to consider real-time and computing power limitations of the embedded platform.
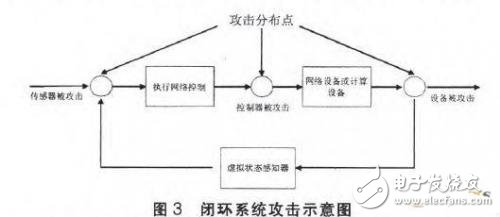
The literature first establishes a typical model of the physical system, simplifying the physical system into a linear system. Secondly, for DOS attacks and spoofing attacks, the attack factors are added based on the original linear system model. As shown in Figure 3, the attack factors may be distributed in different parts of the closed-loop control loop, the sensor part, the actuator part, and the equipment part. Based on different attack factors, a control algorithm with a state monitor is designed to detect the operating state of the system. The algorithm can make the system still in a secure state when it is served when it is rejected. When it is attacked by a spoofing attack, it can detect the attack. The design of the safety controller is currently limited to academic research, and its application in practical systems is not yet mature. This is because the design controller needs to establish a relatively accurate physical model, and the generality is not high. The possible solution is to use the mode of the main controller and the safety controller in the hardware design of the controller, and use the bypass information, such as program execution time, code execution order, etc., if the main controller and the safety controller bypass information Inconsistent, take security measures.
3, the conclusion
This paper first studies the industry characteristics and requirements of industrial control systems, and analyzes the threats faced by industrial control systems. Secondly, after deep understanding of relevant industry information security assurance application regulations, it introduces the information security status applicable to industrial control systems. The three perspectives of protection, protocol security and controller design analyze the current research ideas and have certain reference significance.
Lithium Ior Batteries For Electric Lifting Platform
Shenzhen Sunbeam New Energy Co., Ltd , https://www.sunbeambattery.com